
So what is de-serialization? What are serialization attacks? What is serialization? What is serial? Ok ok, hold your horses, kemosabe…will start from the beginning, this is serial:

Now that the hard part is out of our way, lets start dissecting the rest. Common explanation: Serialization is merely representing object as a stream of bits and bytes. We use it for transferring objects between different systems. But hey, aren’t all objects streams of bits and bytes, you may ask?

Yes! Correct! In the end, they are…So? It’s all about formats. Even when you save a simple “hi there” text object, it gets transformed into a series of 0s and 1s and saved in such a “serialized” state on your local machine. Approximately the same happens (sometimes) when we transmit data from our application to another. Also, not all transmission formats are bits and bytes (binary) either, like in PHP. Different languages have their own different serialization/de-serialization implementations. Folks use different serialized formats for reliable and effective transmission (so that no bits / data gets lost during various encodings/decoding/input transformation etc that can happen to the transmitted info along the way).
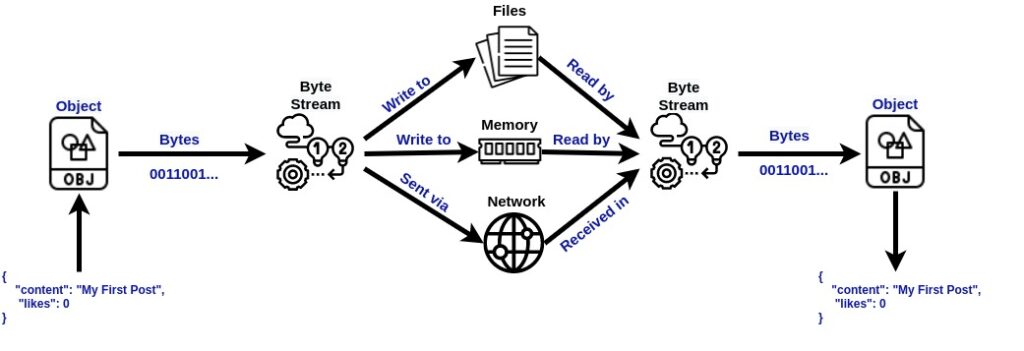
So you may think at this point, where can the vulnerability hide? Lets think logically…at some point our serialized objects will have to get DE-SERIALIZED!!!!! That’s right. That’s the soft underbelly, that’s the Achilles heel. When serialized objects get Deserialized on the other end.
Now, it’s not an easy process, of course…couple of things need to happen:
- You need to spot the serialized data that the application is sending to the other end (server).
- You need to figure out the format that was used to serialize data…hey, there can be ton of different formats, although..there are some standard ones as well.
- The application needs to de-serialize the data and use/handle it in an insecure manner.
So basically, stars will have to align for us to get it done…not one of the easiest vulns, but sure one of the more dangerous ones.

